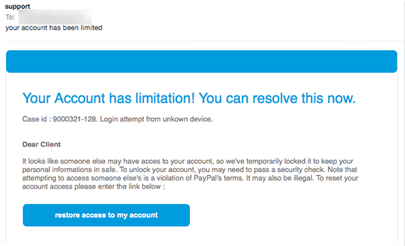
If you’re like me, you get lots of spam, and a lot of it harbors a malicious intent. People are constantly trying to get me to cough up user ids and passwords, bank accounts, or unwittingly install malware on my computer. I’m pretty skeptical about email and so far (knock on wood) I’ve managed to avoid falling for them.
For the most part, that’s not hard to do. Most people sending phishing email do an incredibly bad job of mimicking the real thing, so it usually doesn’t look good. Every once in a while one looks really good, but that just gets me more excited to find its tell. And they all have tells … which means that, if you’re really good at looking for them, and extremely diligent, you should never fall victim to one of these scams.